How Network Access Control Solutions Enhance Regulatory Compliance
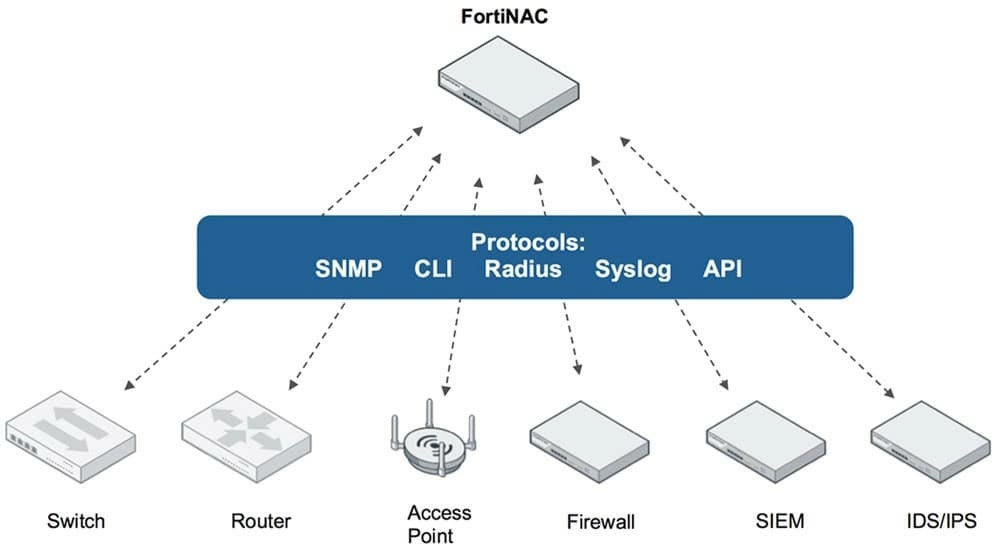
Network Access Control Solutions
Network access control solutions verify user and device identities to limit access to the organization’s network. They also inspect devices to assess their security posture and ensure policy compliance.
NAC solutions are essential for facilitating BYOD, work-from-anywhere, and remote working policies, protecting sensitive data, and providing guest users with a smooth connectivity experience. They also prevent malware attacks by blocking unauthorized or risky devices.
Enhanced Visibility and Control
Many organizations pursue network access control (NAC) solutions for security reasons, but they may also be compelled by regulatory requirements to do so. NAC solutions help to ensure that only authenticated users and devices can access the network. They can also restrict lateral movement within the network, protecting against cyber attacks and reducing the impact of compromised devices. They can even prevent IoT devices from communicating, which helps eliminate the risk of rogue access points and other forms of shadow IT.
For example, a device can connect to the company’s network without registration, creating a vulnerability. NAC solutions can force devices, including BYOD and guest equipment, to provide proper user authentication methods and security postures before granting them network access, reducing the number of potential vulnerabilities that attackers could exploit. Additionally, they can monitor for non-compliant devices trying to access the network, denying them access until they can navigate automated remediation processes. This strengthens security and saves IT and Help Desk costs while maintaining regulatory compliance.
Automated Response
NAC solutions identify and verify devices, ensuring only compliant users or devices can access the network. This minimizes unauthorized access and cyber-attacks by preventing malware infections, data breaches, and other threats. This also helps organizations achieve
and maintain regulatory compliance with mandates such as HIPAA, SOX, or PCI-DSS, helping reduce fines that may result from non-compliance.
NAC’s pre-admission and post-admission network access control features allow admins to approve/deny access automatically per-user or device. This can dramatically cut the time and accompanying costs of authentication and authorization. It is particularly important during high-stakes moments, such as during a major cyber attack, when limiting lateral movement and the extent of the damage from exploited vulnerabilities would be advantageous.
Some NAC solutions can also be configured in a monitor mode, allowing admins to observe policies’ impact before they are implemented and enforced, allowing for greater agility and reduced risk. Additionally, NAC can provide capabilities that automate isolating and removing unpatched machines from the network to help reduce IT workload.
Streamlined Onboarding
Today’s organizations face many challenges in safeguarding devices, physical infrastructure, applications, and data. Bring your device regulations (BYOD), increasing remote work, and a significant third-party ecosystem require an IT team to constantly authenticate users and their devices before allowing access to the organization network.
Network access control solutions automate the process, eliminating the need for IT to manually approve or deny network access on a per-user or device basis. NAC tools also prevent unwanted traffic from entering the network by ensuring all devices meet security policies before they gain admission.
NAC tools leverage information other network security systems collect to identify user identities and connected devices. This enables the NAC solution to implement a more precise level of access control, ensuring that only authorized devices are allowed into sensitive areas of the network. Additionally, a NAC solution can provide the capability to
quarantine dangerous devices from gaining full network access by limiting them to throttled internet-only access — ensuring guests and contractors don’t have access to company data. This reduces the attack surface and limits the impact of any breach.
Reduced Attack Surface
With the proliferation of BYOD and remote work policies, organizations connect myriad devices to their networks. NAC solutions reduce an organization’s attack surface by ensuring devices are compliant with corporate security policies before granting access to corporate resources. NAC solutions can also help to restrict network access to applications and data, minimizing the impact of cyber attacks that exploit these areas of the network.
Most NAC solutions use pre-admission and post-admission controls to provide maximum protection for a network. This defense-in-depth approach helps to block as many threats as
possible from entering the network. When a device does get onto the network, NAC can be configured to immediately detect suspicious activity and take action, such as isolating the infected endpoint or enforcing internal security policies. The policy-based model used by most NAC solutions provides great flexibility and scalability, with admins able to change network access rules instantly for tens of thousands of devices. This is a critical capability when responding to fast-moving attacks like worms and ransomware. For more information about boosting your NAC solution, check out how Varonis can help!
Enhanced Security
Today’s crowded network environments are full of users and devices that must be managed securely. NAC solutions automate the verification of users and devices as they attempt to join a corporate network, helping to ensure that they meet security policies and requirements.
A good NAC solution will allow IT staff to define access policies based on user groups, device types, or network areas. This allows for granular control over access, minimizing the attack surface and protecting critical information.
NAC also helps reduce malware spread by ensuring that infected devices are blocked from joining the network and remain isolated until they can be patched or cleaned. Some NAC solutions can be integrated with other cybersecurity tools, such as network firewalls, security information and event management (SIEM), and identity and access management (IAM) solutions to provide a single line of defense and unify security posture into a coherent whole.
The best NAC solutions will be scalable and integrate with various infrastructure devices, including switches, routers, and wireless access points. Some will use agentless technologies that do not require software installations on endpoints, and others will incorporate dissolvable techniques to allow short-term network access. At the same time, a device undergoes a security check.
Also read – The Heiress Returns And Revenge Novel








